On Tuesday, March 3, 2015, researchers announced a new SSL/TLS vulnerability called the FREAK attack. It allows an attacker to intercept HTTPS connections between vulnerable clients and servers and force them to use weakened encryption, which the attacker can break to steal or manipulate sensitive data.
You can check whether your browser is vulnerable using FREAK Client Test Tool.
Chrome for Windows and all versions of Firefox are known to be safe. However, even if your browser is safe, certain third-party software, including some anti-virus products and adware programs, can expose you to the attack by intercepting TLS connections from the browser. If you are using a safe browser but our client test says you’re vulnerable, this is a likely cause.
In addition to browsers, many mobile apps, embedded systems, and other software products also use TLS. These are also potentially vulnerable if they rely on unpatched libraries or offer RSA_EXPORT cipher suites.
Clients
Update (Mar. 5): Browsers are vulnerable to the FREAK attack because of bugs that allow an attacker to force them to use weak, export-grade encryption. One example is the OpenSSL bug described in CVE-2015-0204, but some other TLS libraries have similar problems. Far more browsers are vulnerable to the FREAK attack than was initially thought when the attack was announced, including:
Google already released an updated version of the Chrome browser for Mac systems, meanwhile Safari on Mac OS and iOS isn’t vulnerable to the FREAK flaw.
To determine if your browser is vulnerable visit freakattack.com.

All Windows systems are vulnerable to the FREAK attack
According to a security advisory published by Microsoft all supported versions of Windows are affected by the recently discovered FREAK vulnerability
FREAK is major security SSL/TLS vulnerability recently discovered that for more than a decade left users of Apple and Google devices vulnerable to hacking when they visited millions of legitimate and secure websites.
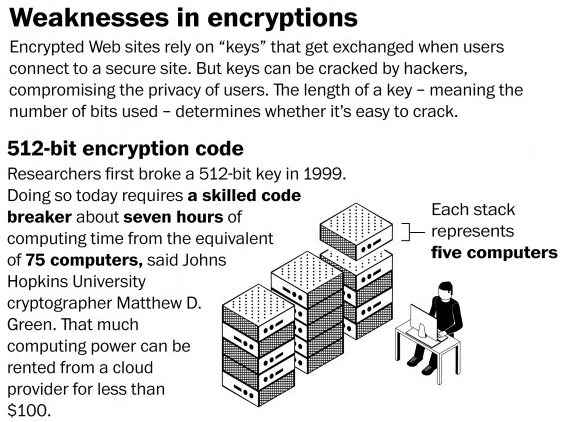
The critical vulnerability codenamed FREAK (CVE-2015-0204), also known as Factoring Attack on RSA-EXPORT Keys, could be exploited by threat actors to run man-in-the-middle attacks on encrypted traffic when Internet users visited supposedly secured websites. By exploiting the FREAK flawan attacker can force clients to use older and weaker encryption, then he can crack the traffic protected with 512-bit key encryption in a few hours. Once decrypted the traffic a threat actor can steal sensitive information or launch an attack by injecting malicious code.
Unfortunately, the impact of the vulnerability could be dramatic for Microsoft systems, according to a security advisory published by the company FREAK vulnerability resides in the Microsoft Secure Channel (Schannel)stack.
Microsoft users are warned, hackers that share the same network could exploit the Freak flaw and force the software using Schannel component (i.e. Internet Explorer) to use weak encryption over the web.
It is important to clarify that the attack could be effective if the server hosting the website visited by victims still supporting 1990s-era “export-grade” cryptography or 512-bit RSA.
A scan of more than 14 million websites that support the SSL/TLS protocols has revealed that the FREAK vulnerability affects nearly 36 percent of SSL WEBSITES.
The Windows version affected by the FREAK vulnerability (CVE-2015-1637) are:
Microsoft confirmed that its experts are “actively working” to fix the issue and to protect its users from cyber attack exploiting the FREAK vulnerability.
You can check whether your browser is vulnerable using FREAK Client Test Tool.
Chrome for Windows and all versions of Firefox are known to be safe. However, even if your browser is safe, certain third-party software, including some anti-virus products and adware programs, can expose you to the attack by intercepting TLS connections from the browser. If you are using a safe browser but our client test says you’re vulnerable, this is a likely cause.
In addition to browsers, many mobile apps, embedded systems, and other software products also use TLS. These are also potentially vulnerable if they rely on unpatched libraries or offer RSA_EXPORT cipher suites.
Clients
Update (Mar. 5): Browsers are vulnerable to the FREAK attack because of bugs that allow an attacker to force them to use weak, export-grade encryption. One example is the OpenSSL bug described in CVE-2015-0204, but some other TLS libraries have similar problems. Far more browsers are vulnerable to the FREAK attack than was initially thought when the attack was announced, including:
| Vulnerable Browser | Status |
| Internet Explorer | Security advisory |
| Chrome on Mac OS | Patch available now |
| Chrome on Android | |
| Safari on Mac OS | Patch expected next week |
| Safari on iOS | Patch expected next week |
| Stock Android Browser | |
| Blackberry Browser | |
| Opera on Mac OS | |
| Opera on Linux |
Google already released an updated version of the Chrome browser for Mac systems, meanwhile Safari on Mac OS and iOS isn’t vulnerable to the FREAK flaw.
To determine if your browser is vulnerable visit freakattack.com.

All Windows systems are vulnerable to the FREAK attack
According to a security advisory published by Microsoft all supported versions of Windows are affected by the recently discovered FREAK vulnerability
FREAK is major security SSL/TLS vulnerability recently discovered that for more than a decade left users of Apple and Google devices vulnerable to hacking when they visited millions of legitimate and secure websites.
The critical vulnerability codenamed FREAK (CVE-2015-0204), also known as Factoring Attack on RSA-EXPORT Keys, could be exploited by threat actors to run man-in-the-middle attacks on encrypted traffic when Internet users visited supposedly secured websites. By exploiting the FREAK flawan attacker can force clients to use older and weaker encryption, then he can crack the traffic protected with 512-bit key encryption in a few hours. Once decrypted the traffic a threat actor can steal sensitive information or launch an attack by injecting malicious code.

Unfortunately, the impact of the vulnerability could be dramatic for Microsoft systems, according to a security advisory published by the company FREAK vulnerability resides in the Microsoft Secure Channel (Schannel)stack.
“Secure Channel, also known as Schannel, is a security support provider (SSP) that contains a set of security protocols that provide identity authentication and secure, private communication through encryption. Schannel is primarily used for Internet applications that require secure Hypertext Transfer Protocol (HTTP) communications.”
Secure Channel is vulnerable to the FREAK encryption-downgrade attack, the bad news is that affects all supported releases of Microsoft Windows, as reported in the advisory.“Microsoft is aware of a security feature bypass vulnerability in Secure Channel (Schannel) that affects all supported releases of Microsoft Windows. Our investigation has verified that the vulnerability could allow an attacker to force the downgrading of the cipher suites used in an SSL/TLS connection on a Windows client system. The vulnerability facilitates exploitation of the publicly disclosed FREAK technique, which is an industry-wide issue that is not specific to Windows operating systems. When this security advisory was originally released, Microsoft had not received any information to indicate that this issue had been publicly used to attack customers.” states the advisory.
The Windows version affected by the FREAK vulnerability (CVE-2015-1637) are:- Windows Server 2003
- Windows Vista
- Windows Server 2008
- Windows 7
- Windows 8 and 8.1
- Windows Server 2012
- Windows RT
Microsoft users are warned, hackers that share the same network could exploit the Freak flaw and force the software using Schannel component (i.e. Internet Explorer) to use weak encryption over the web.
It is important to clarify that the attack could be effective if the server hosting the website visited by victims still supporting 1990s-era “export-grade” cryptography or 512-bit RSA.
A scan of more than 14 million websites that support the SSL/TLS protocols has revealed that the FREAK vulnerability affects nearly 36 percent of SSL WEBSITES.
“Based on some recent scans by Alex Halderman, Zakir Durumeric and David Adrian at University of Michigan, it seems that export-RSA is supported by as many as 5.2% 36.7% (!!!!) of the 14 million sites serving browser-trusted certs. The vast majority of these sites appear to be content distribution networks (CDN) like Akamai. Those CDNs are now in the process of removing export grade suites.” states Matthew Green.
Let’s remind that the “expor-grade” feature was explicitly requested by the U.S. government for overseas export, the situation changed in 2000 due to a modification of the US export laws. Starting from 2000 vendors were allowed to include 128-bit ciphers in the products that were distributed all over the world.The Windows version affected by the FREAK vulnerability (CVE-2015-1637) are:
- Windows Server 2003
- Windows Vista
- Windows Server 2008
- Windows 7
- Windows 8 and 8.1
- Windows Server 2012
- Windows RT
Microsoft confirmed that its experts are “actively working” to fix the issue and to protect its users from cyber attack exploiting the FREAK vulnerability.
“We are actively working with partners in our Microsoft Active Protections Program (MAPP) to provide information that they can use to provide broader protections to customers.” continues the advisory.







